Two of three phishing pages analyzed by Armorblox were hosted on legitimate services to try to sneak past the usual security protection.

Image: weerapatkiatdumrong, Getty Images/iStockphoto
Successful phishing campaigns not only have to convince users of their legitimacy but must find ways to dodge security measures that would ordinarily flag them as suspicious. A report issued on Tuesday by email security provider Armorblox looked at the tactics employed by three recent phishing campaigns and suggests ways to avoid these types of scams.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
For its new report, Armorblox examined three separate phishing attacks that impersonated Facebook, Microsoft and Apple. In each case, the attackers tried to steal the credentials of recipients by claiming that their accounts has been locked or that their subscriptions were about to expire. And in each case, the emails were able to get past security defenses to end up in the inboxes of their targeted victims.
Facebook phishing attack

Image: Armorblox
In this campaign, the phishing email impersonates Facebook to warn a user that their account has been restricted due to security concerns. Using a subject of "Reminder: Account Verification," a sender name of Facebook, and an address of noreply@cc.mail-facebook.com, the email instructs recipients to verify their Facebook account in order to restore full access.
Clicking the link in the email takes the user to a phishing page that looks like the real Facebook login page. If the person actually does sign in, the page captures their phone number or email address and Facebook password.
To work effectively, this campaign uses a variety of tactics, including social engineering, brand impersonation, the compromise of existing email workflows, domain spoofing, and sender name spoofing. The parent name of the page is sliderdoyle.com, which provides a clue to its malicious nature (and is blocked by the major browsers as a deceptive site). However, the page looks similar enough to the real Facebook login portal and conveys a sense of urgency so that some Facebook users may fill out the form without scrutinizing the URL.
The phishing email in this attack got past both Cisco Email Security Appliance and Microsoft's Exchange Online Protection. The email was assigned a Spam Confidence Level of -1 by Microsoft, indicating that it skipped any type of spam filtering.
Microsoft phishing attack
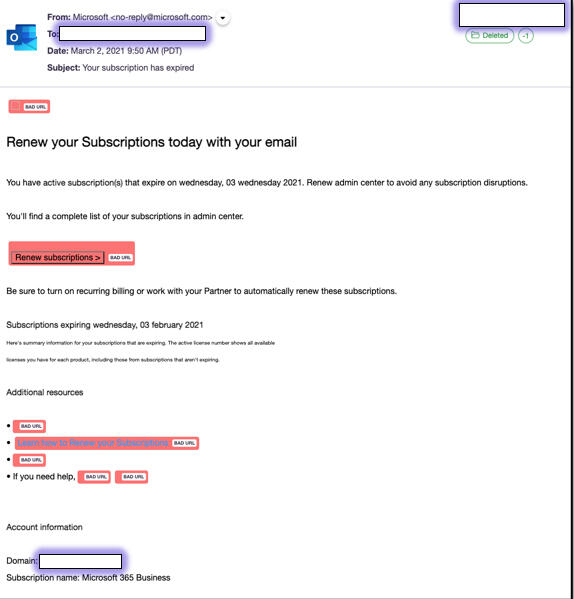
Image: Armorblox
In this one, an email spoofing Microsoft used a subject of "Your subscription has expired" with Microsoft as the sender and the email address as no-reply@microsoft.com. The message told the recipients that their subscriptions were about to expire and that they should sign into the admin center to renew them. Clicking the link in the email takes the user to a phishing page that looks like the Microsoft login portal and prompts people to log in with their Microsoft credentials.
Armorblox noticed two tipoffs indicating that the email was suspicious. The reply-to address is different from the From address, a common ploy used in email attacks. Plus, the URL was not only very long but contained a typo, another sign of a malicious message.
However, other tactics give the campaign an air of legitimacy. The parent domain of the phishing page is support-outlooks.ddns.net, which shows that the attackers hosted the page on DDNS.net, a free dynamic DNS service. The urgency expressed in the message combined with the page's resemblance to the real Microsoft login portal may prompt some recipients to enter their credentials without thinking.
This Microsoft phishing email thwarted both Cisco E Email Security Appliance and Microsoft EOP. The email was assigned a Spam Confidence Level of -1 by Microsoft.
Apple phishing attack

Image: Armorblox
In this campaign, an email impersonating Apple claimed that the recipient's Apple ID had been locked for security reasons and that they would need to verify their account within 12 hours or it would be suspended. The email used a subject of "Re: Your Apple ID has been locked on March 11, 2021 PST" with a reference number, while the sender's name was Appie ID. Though that ID seems like a typo, the misspelling is actually a ploy used to sneak past security techniques like filters and blocklists.
Clicking the link in the email had directed users to a phishing page hosted on Omnisend, an e-commerce email marketing and SMS platform. The attackers used a free trial of Omnisend to set up the phishing page and send their emails, a common tactic that increases the success rate by relying on a legitimate hosting service.
However, this campaign was more amateurish than the ones for Facebook and Microsoft, Armorblox said. After the security firm discovered the attack, the phishing page had already been identified and taken down. The actual phishing email evaded the defenses of Symantec Advanced Threat Protection but got a Spam Confidence Level of 5 from Microsoft, which redirected it to the junk folders of recipients.
As a whole, the three phishing attacks used several tricks to appear legitimate to users as well as to security defenses.
Two of the campaigns added urgency by claiming that the accounts were locked or in some type of jeopardy. The Facebook campaign tried to take advantage of the assumption that most Facebook users don't protect their accounts with multi-factor authentication. The subjects, names, content, and design of the three phishing emails impersonate well-known brands to target specific users. The Microsoft and Apple spoofers hosted their landing pages on regular cloud-based sites to appear legitimate and used free online services to lower their costs.
To protect yourself and your organization from these types of phishing attacks, Armorblox offers three tips.
Augment native email security with additional controls. Two of the phishing emails evaded Microsoft's Exchange Online Protection, with an assigned Spam Confidence Level of -1, meaning they skipped past spam filters. For better coverage against phishing campaigns and other email attacks, invest in technologies that take a different approach to threat detection. Gartner's Market Guide for Email Security covers new approaches and should be a good starting point for your evaluation.
Watch out for social engineering cues. Since we get so many emails from service providers, our brains have been trained to quickly respond to their requested actions. Though easier said than done, learn to engage with these emails in a rational and methodical manner whenever possible. Subject the email to an eye test that includes inspecting the sender name, sender email address, language within the email, and any logical inconsistencies within the email (e.g. Why is the email sender name Appie ID instead of Apple ID? Why is Facebook sending this email to my work account?).
Follow multi-factor authentication and password management best practices. If you haven't already, implement the following best practices:
- Deploy multi-factor authentication on all possible business and personal accounts.
- Don't use the same password on multiple sites or accounts.
- Use a password management program to store your account passwords.
- Avoid using passwords that tie into your publicly available information (date of birth, anniversary date, etc.).
- Don't repeat passwords across accounts or use generic passwords such as your birth date or terms that contain the word "password," "12345," or other obvious strings.
Also see
"traditional" - Google News
March 31, 2021 at 02:44AM
https://ift.tt/39vkbR7
How phishing attacks evade traditional security defenses - TechRepublic
"traditional" - Google News
https://ift.tt/36u1SIt
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini















0 Response to "How phishing attacks evade traditional security defenses - TechRepublic"
Post a Comment